Source: US Northwestern University’s Medill Reports
Security measures apparently do little to deter robbers. Of the 7,272 robberies or attempted robberies in the USA in 2006, 98 percent of victim institutions had an alarm system and/or surveillance cameras.
One man accused of robbing seven Indiana banks told a newspaper earlier this month that his only deterrent to robbing banks was security guards – a rare feature today at US banks.
Instead of career robbers, people from many walks of life are gravitating to robbery, ranging from drug addicts to employed middle-class individuals, according to Gregory Scott, professor of sociology at DePaul University, Chicago.
“We’re coming to the end of the really well-plotted, well-organized bank robbery that results from long-term strategic planning. Now we’re talking about lower-level bank robberies,” he said.
Today’s robbers are spontaneous and opportunistic, according to a 2007 study commissioned by the U.S. Department of Justice, which identified three factors contributing to rising robbery rates: more bank outlets and extended hours creating greater opportunities, robbers' perceptions of banks as a lucrative target and because robberies are usually fast, low risk crimes - in the USA 90% of robberies are successful, although 60% of robbers are eventually caught.
Offering the CSMP - Certified Security Management Professional distance-learning award www.ismi.org.uk
Monday, March 31, 2008
Kidnap News
Read about the latest kidnap stories from around the world
at:
http://claytonconsultants.com/e/2008/03/newsletter/KRE-Monitor-Mar-2008.pdf
at:
http://claytonconsultants.com/e/2008/03/newsletter/KRE-Monitor-Mar-2008.pdf
BlackBerry Warning
British businesses are being told to make certain they accurately configure their BlackBerries, or risk reducing their information-technology security levels.
Online security consultancy NTA Monitor states recent testing revealed that companies are still not making sure the smartphones are locked down. It stresses that BlackBerry infrastructure can be breached if no firewalls are utilized to divide the BlackBerry Enterprise Server (BES) router element from the main BES servers on the inside network. If the BES is jeopardized and the BES router is not separate, it can result in the entire network becoming insecure, NTA says.
RIM vice president of global security Scott Totzke, however, notes that while this strategy might benefit certain BlackBerry clients, it is only one way to protect the devices, and that there is not just one solution for all security needs. He explains that the BlackBerry infrastructure has over 400 configurable security protocols, providing clients the ability to reduce their own risk level. NTA Monitor also suggests that BlackBerry administrators shut off Bluetooth, although Totzke points out that the BlackBerry model permits users to turn on parts of Bluetooth and shut off others, which may be the best response.
Source:
http://news.zdnet.co.uk/hardware/0,1000000091,39365233,00.htm
Online security consultancy NTA Monitor states recent testing revealed that companies are still not making sure the smartphones are locked down. It stresses that BlackBerry infrastructure can be breached if no firewalls are utilized to divide the BlackBerry Enterprise Server (BES) router element from the main BES servers on the inside network. If the BES is jeopardized and the BES router is not separate, it can result in the entire network becoming insecure, NTA says.
RIM vice president of global security Scott Totzke, however, notes that while this strategy might benefit certain BlackBerry clients, it is only one way to protect the devices, and that there is not just one solution for all security needs. He explains that the BlackBerry infrastructure has over 400 configurable security protocols, providing clients the ability to reduce their own risk level. NTA Monitor also suggests that BlackBerry administrators shut off Bluetooth, although Totzke points out that the BlackBerry model permits users to turn on parts of Bluetooth and shut off others, which may be the best response.
Source:
http://news.zdnet.co.uk/hardware/0,1000000091,39365233,00.htm
Security Management Access Control Feature: Learn All about Biometrics at Wikipedia!
 Wikipedia carries a very interesting discourse on developments in biometrics technology, studying this fast-developing field from both a technological and sociological point of view.
Wikipedia carries a very interesting discourse on developments in biometrics technology, studying this fast-developing field from both a technological and sociological point of view.If you are considering installing biometrics, this is an interesting and useful read.
http://en.wikipedia.org/wiki/Biometrics#_note-jain_short_article
Saturday, March 29, 2008
CPP Certification - A Message from a Very Happy CPP-Certified ARC Course Delegate in SE Asia
"Dear David
Just to inform you that I have obtained all the CPE credits required for the three-year recertification term by just attending one ARC security management course. This is a great seller for any CPP holders who want to obtain all the points in the cheapest way possible.”
Just to inform you that I have obtained all the CPE credits required for the three-year recertification term by just attending one ARC security management course. This is a great seller for any CPP holders who want to obtain all the points in the cheapest way possible.”
Data Security - Encryption Keys Can be Compromised for Several Minutes after Switching off Computers, Scientists Find
 Scientists have shown that it is possible to recover the key that unscrambles data from a PC's memory.
Scientists have shown that it is possible to recover the key that unscrambles data from a PC's memory.It was previously thought that data held in so-called "volatile memory" was only retained for a few seconds after the machine was switched off. But the team found that data including encryption keys could be held and retrieved for up to several minutes.
"The real worry is that someone will get hold of your laptop either while it is turned on or while it is in sleeping or hibernation mode," said research scientist Professor Felten.
Camera that "Sees" Through clothes Developed
 A camera capable of detecting drugs, explosives or weapons hidden under people's clothes from up to 25 metres away has been developed in what could be a breakthrough for the security industry.
A camera capable of detecting drugs, explosives or weapons hidden under people's clothes from up to 25 metres away has been developed in what could be a breakthrough for the security industry.The T5000 camera uses what it calls "passive imaging technology" to identify objects by the natural electromagnetic rays - known as Terahertz or T-rays - that they emit.
Read on at:
http://www.itpro.co.uk/security/news/176037/camera-that-sees-through-clothes-developed.html
Friday, March 28, 2008
Thank You for Your Outstanding Support Rendered to Me during the Security Surveying Course!
 "Thank you for your outstanding support rendered to me during the Security Surveying Course."
"Thank you for your outstanding support rendered to me during the Security Surveying Course."A sentiment expressed by one of the eight delegates who participated in the recent Security Surveying and Design Course in Cyprus.
Surveying is a task that almost all security managers are called upon to carry out, but for which few have been formally trained. This Skills for Security-accredited course begins by addressing the security risk and threat analysis process, and explains how to carry out a facility and operational characterization, both essential pre-cursors to undertaking a valid assessment of security measures.
Following a detailed session on security design, the practical phase begins with participants working in syndicates to carry out a survey on a real (working) site. Results are then collated, analysed and written up as a full security survey report, under the close guidance of the tutor. Finally, the groups have to formally present their results, and their report, to a “management team” and respond to questions.
The course is delivered by Peter Horsburgh CPP PSP, who, when not training, is a full-time security surveying consultant on behalf of ARC. Twice a corporate head of security, Peter has surveyed literally hundreds of sites.
This is a very enjoyable, practical and fast-paced course, which will provide you with all the skills and confidence necessary to carry out a full security survey of a large site.
Delegates booked so far represent sectors including financial services and banking, government, retail, manufacturing and property development.
Location: Near Reading, Thames Valley
Dates: 21-25 April 2008
Contact: Janet
Dutch Nationals Overseas - Alert
Holland is likely to come under renewed pressure from the Muslim world in coming days following yesterday’s posting on a video-sharing website of an anti-Islamic film by radical Dutch right-wing MP, Geert Wilders.
Boycotts of Dutch products and services, such as was seen recently with Denmark, cannot be ruled out, and Dutch nationals overseas should be aware of heightened sensibilities and possible reactions to this issue.
Boycotts of Dutch products and services, such as was seen recently with Denmark, cannot be ruled out, and Dutch nationals overseas should be aware of heightened sensibilities and possible reactions to this issue.
Thursday, March 27, 2008
Security Management Training – (And the First Step towards a Degree)

16 security manager delegates from the Far East, the UK, the Middle East and Africa will begin an intensive postgraduate university-accredited security management training programme on Monday 31 March, which could ultimately earn them a work-based learning MSc in Corporate Security Management.
Security Management Stage 1 (31 March – 11 April) is the first of six modules that make up this programme, which is unique in the security management profession.
Under the close guidance of David Cresswell CPP, who is actively engaged in the delivery of postgraduate education in security management in the UK, delegates will study a wide range of core security management subjects, ranging from security risk management, security design, access management, personnel protection, investigations, policies and procedures, manpower management and leadership, change management, crisis management, security strategy planning, crime prevention, information security, anti-terrorism, and surveying.
The next Security Management Stage 1 course takes place 4-15 August 2008. Contact Janet for details.
Security Management Stage 1 (31 March – 11 April) is the first of six modules that make up this programme, which is unique in the security management profession.
Under the close guidance of David Cresswell CPP, who is actively engaged in the delivery of postgraduate education in security management in the UK, delegates will study a wide range of core security management subjects, ranging from security risk management, security design, access management, personnel protection, investigations, policies and procedures, manpower management and leadership, change management, crisis management, security strategy planning, crime prevention, information security, anti-terrorism, and surveying.
The next Security Management Stage 1 course takes place 4-15 August 2008. Contact Janet for details.
A Step too Far?
 “CCTV systems can monitor every room in your home with clear, high visibility images. CCTV surveillance is available for four, nine, or up to 16 rooms in your home. By monitoring your family's security on a CCTV network, you are able to record suspicious activities as they occur. Monitor your yard, front door, garage, even your mailbox.”
“CCTV systems can monitor every room in your home with clear, high visibility images. CCTV surveillance is available for four, nine, or up to 16 rooms in your home. By monitoring your family's security on a CCTV network, you are able to record suspicious activities as they occur. Monitor your yard, front door, garage, even your mailbox.”A step too far? .............
Port Security
 - Ports can be either the target of a terrorist attack, or the conduit for an attack elsewhere.
- Ports can be either the target of a terrorist attack, or the conduit for an attack elsewhere.- Scanners and X-Ray devices used on containers moving through ports would not detect small amounts of radioactive material required for a dirty bomb.
- There is no mandatory minimum standard for supply chain security for shippers moving cargo into the US.
- By writing the correct information on a container manifest, terrorist groups could bring hazardous material into your country without alerting the CBR targeting systems.
- Security programmes' focus on containers has made other kinds of cargo more attractive to terrorists.
- The threat from insiders is being addressed by The Transport Worker Identification Credential, or TWIC Card, scheme which requires port workers to be background checked, and stores biometric information which, from 2009, will be used to periodically ID personnel.
Maritime security is covered in detail in ARC Training’s Maritime Security Management course, 6-10 October 2008. Contact Janet for details.
There is no Fourth Option!
 When disposing of used company hard drives (or flash drives), there are only three options:
When disposing of used company hard drives (or flash drives), there are only three options:1. Put the drive through an industrial disintegrator; or
2. Use an approved (DoD Standard) data elimination program, such as WipeDrive; or
3. Use a special degausser, such as Mag EraSURE ME-P3M.
Simply reformatting the drive and selling it, or donating it, on is not an option. Your company’s most sensitive data can be recovered using tools freely available on the Internet.
This, and other crucial aspects of IT and information security are addressed in the Information and IT Security Workshop, which forms part of ARC Training’s university-accredited Security Management Stage 1 Course.
The workshop can be attended as a stand-alone on-day module on the following dates (or in house on request):
7 April
11 August
24 November
Contact Janet for details.
Tuesday, March 25, 2008
Security Management Training - Forthcoming Events
Security Management Stage 1
31 March – 11 April
31 March – 11 April
The first stage of a university accredited programme which can lead to an MSc
Protection against Explosive Devices Workshop
3 April
Protection against Explosive Devices Workshop
3 April
Best practice in defending against a range of terrorist explosive devices
Information and IT Security Workshop
7 April
Information and IT Security Workshop
7 April
How to protect your company's (and your customers') most sensitive information, and your company's IT assets
Crisis Management Workshop
8 April
An ideal programme for anybody with a practical involvement in this critical area of risk management
Security Surveying and Design
21-25 April
Learn how to DIY!
Security Management Stage 3
12-23 May
The third stage of a university accredited programme which can lead to an MSc
Kidnap Risk Reduction and Response Workshop
14 May
Kidnap Risk Reduction and Response Workshop
14 May
Ideal for security managers and travelling staff alike
Business Espionage and Investigating Information Leaks
19 May
Learn how to catch the information thieves and leakers - most companies have them!
Business Espionage and Investigating Information Leaks
19 May
Learn how to catch the information thieves and leakers - most companies have them!
Retail and Supply Chain Security Management
2-4 June
A new programme developed and delivered by former heads of security for leading UK retailers
Advanced Investigation Techniques
23-27 June
An ideal programme for international delegates - delivered by senior former police investigation instructors
Security Management Stage 2
30 June – 11 July
The second stage of a university accredited programme which can lead to an MSc
Security Risk Management Workshop
30 June
The logical base on which a security management programme should be built
Contact Janet for more information.
Contact Janet for more information.
Monday, March 24, 2008
Credit Card Fraud Rising - Business Travellers Beware
 Losses from credit and debit card fraud jumped 25% last year to reach £535m, driven by a surge in crimes being committed overseas by criminals using stolen UK card details, figures showed today.
Losses from credit and debit card fraud jumped 25% last year to reach £535m, driven by a surge in crimes being committed overseas by criminals using stolen UK card details, figures showed today.There was also a sharp rise in incidents of so-called card-not-present fraud, when people's card details are used to buy goods online, by phone or via mail order.
Read on at:
http://www.guardian.co.uk/money/2008/mar/12/creditcards.scamsandfraud?gusrc=rss&feed=networkfront
Business travellers should be alert to this risk when overseas. To come to check out at a hotel and find that your credit card’s allowance has been reached would be……awkward!
ARC’s one-day Business Travel Security Workshop is intended to make travellers more savvy to the risks they are exposed to during travel, and the means to best mitigate each. The programme runs on 7 July and 20 October, and can also be delivered in house to your travelling staff.
Security Management Training
Letter from course delegate to ARC Training tutor:
Your brilliant way of imparting training always inspires me to such an extent that I can't find words to express. Your ideas on new approaches to security in general and particular to our region were insightful and a great help to me.
Thank you for for your efforts put in making this course a great success and thank you for sending all the material up till now and for sharing your thoughts.
Your brilliant way of imparting training always inspires me to such an extent that I can't find words to express. Your ideas on new approaches to security in general and particular to our region were insightful and a great help to me.
Thank you for for your efforts put in making this course a great success and thank you for sending all the material up till now and for sharing your thoughts.
“High Profile Direct Actions Targeting Industry and Operations” - Coming Soon
Rising Tide's promise for 1st April, which they have labelled Fossil Fools Day. More at:
http://www.fossilfoolsday.org/
http://www.fossilfoolsday.org/
Animal Rights Extremists Using Car Bombs to Terrorise
 Each day might start with the search under your car for a bomb or the shrill ringing of the phone, signalling yet another anonymous death threat. There's the examination of property damage before you've had your morning cup of coffee. Maybe this time it's broken windows, a flooded house or just hateful graffiti. Then there's the sick worry as you send your children to school, knowing they will be stalked, threatened or denigrated in front of their peers. And the fear as you handle the mail each day, wondering if razors or worse await you upon opening it.
Each day might start with the search under your car for a bomb or the shrill ringing of the phone, signalling yet another anonymous death threat. There's the examination of property damage before you've had your morning cup of coffee. Maybe this time it's broken windows, a flooded house or just hateful graffiti. Then there's the sick worry as you send your children to school, knowing they will be stalked, threatened or denigrated in front of their peers. And the fear as you handle the mail each day, wondering if razors or worse await you upon opening it.Read on about animal rights extremists at:
NATO Warns of Cyberattacks against Infrastructure
Source: Silicon.com
NATO's cybersecurity chief told a London conference recently that cyberattacks are as much of a national security threat as missile attacks. Suleyman Anil, head of NATO's Computer Incident Response Capability Coordination Center, told the E-Crime congress that it's virtually impossible to stop a committed cyberattack on a country's online infrastructure. Read on here.
Read a worrying account on this subject from the Guardian online here.
Meanwhile, the Conservatives, the UK opposition political party, want to create a new post of cybersecurity chief inside the Home Office. In addition, the Conservatives seek the establishment of a new center where the public can report online crime, as well as a new Police National Cybercrime Unit and a new unit of cybercrime specialists inside the Crown Prosecution Service. The Conservatives also want to create a new offence where government employees or contractors would also be held responsible for "reckless handling of personal data by government."
NATO's cybersecurity chief told a London conference recently that cyberattacks are as much of a national security threat as missile attacks. Suleyman Anil, head of NATO's Computer Incident Response Capability Coordination Center, told the E-Crime congress that it's virtually impossible to stop a committed cyberattack on a country's online infrastructure. Read on here.
Read a worrying account on this subject from the Guardian online here.
Meanwhile, the Conservatives, the UK opposition political party, want to create a new post of cybersecurity chief inside the Home Office. In addition, the Conservatives seek the establishment of a new center where the public can report online crime, as well as a new Police National Cybercrime Unit and a new unit of cybercrime specialists inside the Crown Prosecution Service. The Conservatives also want to create a new offence where government employees or contractors would also be held responsible for "reckless handling of personal data by government."
Organisations Failing on Personal Data Security, Consumers Say
Source: ComputerWeekly.com
European consumers say businesses and governments are failing to protect their personal information online. A survey commissioned by VeriSign found that 57% of UK respondents said banks, retailers and the government were failing to do enough to protect their data. This was the highest percentage in Europe, with the level being 44% in Germany, 31% in Sweden, 27% in France and 20% in Denmark.
Recent high-profile business and government data losses may have affected the UK figure.
The overall levels were much higher when it came to personal fears about the threat of identity theft.
These were:
- 79% in Germany
- 78% in the UK
- 70% in France
- 55% in Sweden
- 41% in Denmark
European consumers say businesses and governments are failing to protect their personal information online. A survey commissioned by VeriSign found that 57% of UK respondents said banks, retailers and the government were failing to do enough to protect their data. This was the highest percentage in Europe, with the level being 44% in Germany, 31% in Sweden, 27% in France and 20% in Denmark.
Recent high-profile business and government data losses may have affected the UK figure.
The overall levels were much higher when it came to personal fears about the threat of identity theft.
These were:
- 79% in Germany
- 78% in the UK
- 70% in France
- 55% in Sweden
- 41% in Denmark
Thursday, March 20, 2008
Business Continuity Management - Bird Flu Latest
The high level of avian flu viruses now in widespread in Indonesia has raised the risk that they could mutate and trigger a human influenza pandemic, United Nations Food and Agriculture Organization (FAO) Chief Veterinary Officer Joseph Domenech said Tuesday.
"I am deeply concerned that the high level of virus circulation in birds in the country could create conditions for the virus to mutate and to finally cause a human influenza pandemic," Domenech said in a statement.
Read more at:
http://hstoday.us/index.php?option=com_content&task=view&id=2435&Itemid=149
"I am deeply concerned that the high level of virus circulation in birds in the country could create conditions for the virus to mutate and to finally cause a human influenza pandemic," Domenech said in a statement.
Read more at:
http://hstoday.us/index.php?option=com_content&task=view&id=2435&Itemid=149
Maritime Security Management – Port Security in the US
TWIC, C-TPAT, CBP, FAST, SAFE……..
Read the latest developments in port security in the US in SecurityManagenment online:
http://www.securitymanagement.com/article/measured-steps-toward-safer-ports
ARC’s one-week TRANSEC-accredited Maritime Security Management Course, 6-10 October, covers all of the ISPS port security requirements, blended into mix of corporate security management best practice. Contact Janet for details.
Read the latest developments in port security in the US in SecurityManagenment online:
http://www.securitymanagement.com/article/measured-steps-toward-safer-ports
ARC’s one-week TRANSEC-accredited Maritime Security Management Course, 6-10 October, covers all of the ISPS port security requirements, blended into mix of corporate security management best practice. Contact Janet for details.
Wednesday, March 19, 2008
Increased Terrorism Threat in Holland - Osama Threatens EU

The Dutch government says it has raised the terrorism alert level from "limited" to "substantial" because of "increased international threats", a justice ministry spokesman said last week.
Meanwhile, supermarkets in the UAE and Oman have stopped selling Danish products to protest against the republishing in Denmark of a controversial newspaper cartoon of the Prophet Mohammed. Printing any image of the Prophet is offensive to the sacred beliefs of 1.5 billion Muslims and has, according to Muslim leaders, caused distress to the followers of the faith across the world.
Yesterday the controversy deepened when Osama Bin Laden pledged the support of his Al-Qaeda organisation against the blasphemy. In a new audio message warning against the re-printing of the cartoons he threatened the EU.
For more on this story click the link below:
Security Management Training: I Found the Course Very Professional and Very Useful
 Comment about the recent IT Security and Incident Response Course:
Comment about the recent IT Security and Incident Response Course:"I found the course very professional and very useful, prior to attending I thought this may be over my head, however it was not technical at all and made me think, in a different way about protecting our business. This course really identifies what information you can get from a computer and how it can be used in your investigation. Excellent course, very worth while attending."
The next IT Security and Incident Response Course, led by IT forensics expert, author and broadcaster Ed Wilding, takes place 12-13 November. No detailed prior IT knowledge is required. The course is aimed at anybody, security manager or investigator, who may be involved in an investigation where IT–based data has been the target of a crime, or where IT assets have been used in the commission of a crime, such as fraud, unauthorised data manipulation etc.
Contact Janet for details.
Top Ten Email Scams
Source: ComputerWeekly.com
Security Software McAfee's AVERT labs have reported the top ten phishing scams, the top brands targeted by phishing scams, and the top three internet threats for February 2008.
The web security software firm's labs said the top ten phishing e-mail headers were:
1. Tax Notification
2. Notification from Billing Department
3. NatWest Bank: please confirm your data
4. please confirm your data
5. NatWest Bank customer service: online form released
6. HSBC Bank: please confirm your data!
7. HSBC Bank: official information
8. HSBC Bank customer service: please confirm your data!
9. please confirm your data.
10. please confirm your data!
McAfee said the top brands targeted by phishing scams in February were:
HSBC - 40%
CitiBank - 38%
Natwest - 16%
Bank of America - 6%
The most prevalent internet threats infecting computers in February were:
VBS/Psyme (Trojan virus)
Adware-ZangoSA (adware/malware program)
JS/Wonka (Trojan virus)
Security Software McAfee's AVERT labs have reported the top ten phishing scams, the top brands targeted by phishing scams, and the top three internet threats for February 2008.
The web security software firm's labs said the top ten phishing e-mail headers were:
1. Tax Notification
2. Notification from Billing Department
3. NatWest Bank: please confirm your data
4. please confirm your data
5. NatWest Bank customer service: online form released
6. HSBC Bank: please confirm your data!
7. HSBC Bank: official information
8. HSBC Bank customer service: please confirm your data!
9. please confirm your data.
10. please confirm your data!
McAfee said the top brands targeted by phishing scams in February were:
HSBC - 40%
CitiBank - 38%
Natwest - 16%
Bank of America - 6%
The most prevalent internet threats infecting computers in February were:
VBS/Psyme (Trojan virus)
Adware-ZangoSA (adware/malware program)
JS/Wonka (Trojan virus)
Perimeter Security - Don’t Become an April Fool on 1st April!
 In November last year 15 Greenpeace activists were arrested when protesting at a power station in southeast Australia over climate change. The protestors entered the Munmorah power station on the Central Coast of the state of New South Wales Thursday morning, and several of them attached themselves to the conveyor belts used to feed coal into the facility, Australian Broadcasting Corporation radio reported. Another protester painted the slogan "Coal kills" on the roof of the station.
In November last year 15 Greenpeace activists were arrested when protesting at a power station in southeast Australia over climate change. The protestors entered the Munmorah power station on the Central Coast of the state of New South Wales Thursday morning, and several of them attached themselves to the conveyor belts used to feed coal into the facility, Australian Broadcasting Corporation radio reported. Another protester painted the slogan "Coal kills" on the roof of the station.In similar incidents, a coal-fired power station in the Czech Republic and another in the UK were invaded by protestors, who tried to stop production.
Environmentalist groups around the world have named 1st April as a day of protest under the banner “Fossil Fuels Day”. If you are in the power generating or hydrocarbons industry, you should be alert to the risk of perimeter invasion.
A Radiological Attack Takes a Step Closer?
 Colombia last month accused FARC rebels of planning to make a "dirty bomb" with radioactive material, threatening the entire Latin American region. The charges by Vice-President Francisco Santos, at the United Nations-sponsored Conference on Disarmament, marked a dramatic turn in a regional crisis that has seen Venezuela and Ecuador cut diplomatic ties with Colombia.
Colombia last month accused FARC rebels of planning to make a "dirty bomb" with radioactive material, threatening the entire Latin American region. The charges by Vice-President Francisco Santos, at the United Nations-sponsored Conference on Disarmament, marked a dramatic turn in a regional crisis that has seen Venezuela and Ecuador cut diplomatic ties with Colombia.The US DNS warns that use of a dirty bomb could result in radioactive contamination of several city blocks to an entire city. The extent of the contamination depends upon a number of factors including the size of the explosive, the amount and type of radioactive material used, and weather conditions. Cleanup of the contamination could cost millions of dollars and take weeks to months to complete.
If you have facilities in a major built-up area in which the threat of terrorist is assessed to exist, this should be a scenario envisaged in your business continuity plan.
ARC’s Phil Wood MBE is both a specialist in both business continuity planning and chemical, biological and radiological weapons defence, and would be happy to provide expert advice in updating your plans accordingly. Click here to contact Phil.
Click here for the DHS factsheet.
Take Care to Ensure your Contractors are Taking Care of your Information – Another Horror Story
Computer equipment containing the private financial data of every employee of the Los Angeles Department of Water and Power was stolen in February, prompting the utility to pay for a credit monitoring service for each of its 8,275 workers. The equipment was stolen from a private DWP contractor.
A spokesman for the International Brotherhood of Electrical Workers Local 18, the union that represents DWP employees, said that his workers were "shocked and upset" by the loss of the data. "They believe this is a direct result of the mania for outsourcing that the DWP has had," said Bob Cherry, a communications consultant for the union. "The DWP should have been paying more attention to the potential impact of sensitive data like this getting sent to outside vendors."
Source: LA Times
A spokesman for the International Brotherhood of Electrical Workers Local 18, the union that represents DWP employees, said that his workers were "shocked and upset" by the loss of the data. "They believe this is a direct result of the mania for outsourcing that the DWP has had," said Bob Cherry, a communications consultant for the union. "The DWP should have been paying more attention to the potential impact of sensitive data like this getting sent to outside vendors."
Source: LA Times
Tuesday, March 18, 2008
Business Continuity Management and Emergency Planning – Free Guide Focussed on Practical Steps
 A great guide on emergency management and business continuity planning can be found at the following link:
A great guide on emergency management and business continuity planning can be found at the following link:http://www.nypdshield.org/public/emergency.nypd
What makes the guide so useful is that it focussed on the proactive practical steps that can and should be taken, and comes with useful forms, checklists and templates, and is more user friendly than some of the detailed text in the various national standards.
Thanks to Andrew Kelly in Dubai for finding this.
Security Management Training and Anti-Terrorism Awareness – The Insider Threat
 Although statistically, your organisation is probably unlikely to be the victim of a direct terrorist attack, you may well become an indirect victim, especially if you are located in a built-up area where a threat is know to exist, such as London.
Although statistically, your organisation is probably unlikely to be the victim of a direct terrorist attack, you may well become an indirect victim, especially if you are located in a built-up area where a threat is know to exist, such as London.The Corporate Response to Terrorism Workshop, a follow-on programme from The Protection against Explosive Devices Workshop, examines the key elements of a corporate antiterrorism strategy. One of the areas addressed is the increased threat from insiders, who may have been planted inside your organisation for the purposes of target identification and hostile reconnaissance. Sounds to far fetched to be true?
On 10th March the UK Police Oracle reported on allegations that a sleeper cell of Al-Qaeda spies has infiltrated London’s Metropo0litan Police, and is being kept under surveillance by security services. MI5 has apparently identified 4 officers who, it is believed, have been passing secrets to terrorists.
Diary dates:
The Protection against Explosive Devices Workshop
3 April, 7 August, 20 November
The Corporate Response to Terrorism Workshop
3 July, 16 October
Contact Janet for details or to make a booking.
Proprietary Information Risk- There Is Some Malware Circulating on the Internet That Is Impossible for an Automated Program to Remove
“I’m here to tell you there is some malware circulating on the Internet that is impossible for an automated program to remove,” said Janie Whitty, administrator of the Lavasoft Online Support forums who works with malware victims.
Read on at: http://www.gcn.com/online/vol1_no1/45763-1.html
Read on at: http://www.gcn.com/online/vol1_no1/45763-1.html
ID Theft Focus - Please Ensure Your Company’s Name Does Not Appear on this Website!
 Attrition.org has established itself as the whistleblower on organizations that loose sensitive personal data, whether on laptops, CDs, flash drives etc. To quote from the site:
Attrition.org has established itself as the whistleblower on organizations that loose sensitive personal data, whether on laptops, CDs, flash drives etc. To quote from the site:“In what has become a regular occurrence, companies, universities, and various government entities are collecting your personal information (sometimes without your knowledge or consent), and subsequently letting it fall into the hands of the bad guys.”
If you loose data and the story gets into the press, the news will filter onto the attrition website and remain there forever, readily available at the fingertips of prosecution lawyers, information commissioners, and, of course, your CEO!
Security Managers - Learn How to Better Communicate with the Boss!
Security Managers - Learn how to better communicate with the boss here:
http://www2.csoonline.com/exclusives/column.html?CID=33362
Selling security to the Board is a key message in ARC Training security management courses. For more information, and to discuss which is the correct training programme to best suit your needs, contact Janet.
http://www2.csoonline.com/exclusives/column.html?CID=33362
Selling security to the Board is a key message in ARC Training security management courses. For more information, and to discuss which is the correct training programme to best suit your needs, contact Janet.
Saturday, March 15, 2008
Espionage Alert. What Sensitive Personal Information about Your Key Executives is Lodged with Medical Services?
According to a recent article in Federal Computer Week, foreign criminal hackers are targeting American health records.
Mark Walker of DHS Critical Infrastructure Protection Division recently told a National Institute of Standards and Technology workshop that the hackers' primary motive seems to be espionage. For example, any health problems among the nation's leaders would be of interest to potential enemies, he said.
Walker cited two events from 2007. In one, a virus was placed on the Centers for Disease Control and Prevention Web site. In another, there was a known data breach in the Tricare records for the Military Health System.
Obtaining sensitive personal information about persons in key positions and then blackmailing them in return for information is a tactic probably more widespread often than many people realise!
Mark Walker of DHS Critical Infrastructure Protection Division recently told a National Institute of Standards and Technology workshop that the hackers' primary motive seems to be espionage. For example, any health problems among the nation's leaders would be of interest to potential enemies, he said.
Walker cited two events from 2007. In one, a virus was placed on the Centers for Disease Control and Prevention Web site. In another, there was a known data breach in the Tricare records for the Military Health System.
Obtaining sensitive personal information about persons in key positions and then blackmailing them in return for information is a tactic probably more widespread often than many people realise!
Friday, March 14, 2008
Business Continuity Focus – Are You Prepared for a Bird Flu Pandemic
 Bird flu has been less prominent in the news lately, but the threat of a global pandemic remains real. The last global flu pandemic occurred in 1918, killing tens of millions of people in the USA and Europe. The current epicentre appears to be in South/South East Asia. Of the 200+ people killed so far by the virus, almost half have been in Indonesia.
Bird flu has been less prominent in the news lately, but the threat of a global pandemic remains real. The last global flu pandemic occurred in 1918, killing tens of millions of people in the USA and Europe. The current epicentre appears to be in South/South East Asia. Of the 200+ people killed so far by the virus, almost half have been in Indonesia.Some of the more relevant recent stories about the H5N1 virus, relating to possible vaccinations, bird flu global hot spots and other facts and figures, can be found at the following links:
http://www.kansascity.com/news/nation/story/498813.html
http://news.bbc.co.uk/1/hi/health/7170365.stm
http://news.bbc.co.uk/1/hi/sci/tech/7252923.stm
http://news.bbc.co.uk/1/hi/health/7240636.stm
Contact ARC to discuss your business continuity training needs.
Security Management – Do Women Make Better Leaders? New Research Confirms What Every Woman Knew Already!

Source: Business Week Magazine
Twenty-five years after women first started pouring into the labor force - and trying to be more like men in every way, from wearing power suits to picking up golf clubs - new research is showing that men ought to be the ones doing more of the imitating. In fact, after years of analyzing what makes leaders most effective and figuring out who's got the Right Stuff, management gurus now know how to boost the odds of getting a great executive: Hire a female.
By and large, studies show that women executives, when rated by their peers, underlings, and bosses, score higher than their male counterparts on a wide variety of measures - from producing high-quality work to goal-setting to mentoring employees. Using elaborate performance evaluations of execs, researchers found that women got higher ratings than men on almost every skill measured.
Intrigued – read on here.
Twenty-five years after women first started pouring into the labor force - and trying to be more like men in every way, from wearing power suits to picking up golf clubs - new research is showing that men ought to be the ones doing more of the imitating. In fact, after years of analyzing what makes leaders most effective and figuring out who's got the Right Stuff, management gurus now know how to boost the odds of getting a great executive: Hire a female.
By and large, studies show that women executives, when rated by their peers, underlings, and bosses, score higher than their male counterparts on a wide variety of measures - from producing high-quality work to goal-setting to mentoring employees. Using elaborate performance evaluations of execs, researchers found that women got higher ratings than men on almost every skill measured.
Intrigued – read on here.
Information Security – Don’t Give Foreign Companies Permission to Spy on Your Company’s Most Sensitive Data, or You Could Be out of a Job!
CERT, the world-renowned Carnegie Mellon University computer security team has issued a warning about software end-user licence agreements (EULA), which virtually all of us sign without reading. EULAs are legal contracts, and the vendor or developer may include almost any conditions.
Some EULAs, it seems, are less than standard. For example, in ticking the “I agree” box, you may be agreeing to:
Giving the vendor permission to monitor your computer activity and communicate the information back to the vendor or to another third party. This may put sensitive corporate and ID-related data at risk of security breach.
Allowing vendors to install, or allow 3rd parties to install, additional software programs on your computer. This software may be unnecessary, may affect the functionality of other programs on your computer, and may introduce security risks.
The need has never been greater for somebody within your organisations to take control of
a) What software employees are downloading onto their laptops, and
b) What work related data is stored and processed on home PCs.
In the case of the latter, the majority of home PCs are compromised in some way by peer-to-peer software, spyware or botnets and therefore should never be used to store any company data, the disclosure of which would cause embarrassment to your company – and in the UK, possibly result in a huge fine.
Some EULAs, it seems, are less than standard. For example, in ticking the “I agree” box, you may be agreeing to:
Giving the vendor permission to monitor your computer activity and communicate the information back to the vendor or to another third party. This may put sensitive corporate and ID-related data at risk of security breach.
Allowing vendors to install, or allow 3rd parties to install, additional software programs on your computer. This software may be unnecessary, may affect the functionality of other programs on your computer, and may introduce security risks.
The need has never been greater for somebody within your organisations to take control of
a) What software employees are downloading onto their laptops, and
b) What work related data is stored and processed on home PCs.
In the case of the latter, the majority of home PCs are compromised in some way by peer-to-peer software, spyware or botnets and therefore should never be used to store any company data, the disclosure of which would cause embarrassment to your company – and in the UK, possibly result in a huge fine.
Houston at Elevated Risk of a Bioterrorism Attack?
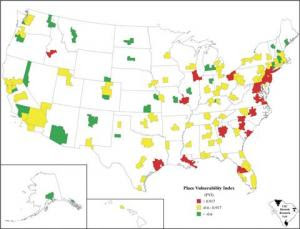 A University of Arizona researcher has created a new system to dramatically show American cities their relative level of vulnerability to bioterrorism, according to the online magazine Science Today.
A University of Arizona researcher has created a new system to dramatically show American cities their relative level of vulnerability to bioterrorism, according to the online magazine Science Today.Walter W. Piegorsch, an expert on environmental risk, has placed 132 major cities -- from Albany, N.Y., to Youngstown, Ohio -- on a color-coded map that identifies their level of risk based on factors including critical industries, ports, railroads, population, natural environment and other factors.
Read on here.
Thursday, March 13, 2008
2008 Promises to Be a Bad Year for Computer Users, But Help Is on Hand
 2008 promises to be a bad year for computer users, especially those who use laptops and those in small businesses. Hackers are fast being replaced by organised criminal gangs and hostile state intelligence services, who are using the expertise of IT professionals to try to break into your systems to steal data. The weakest links are often inexperienced workstation users, or those who like to forward “funny” emails, laptop users, those who use home PCs for work purposes, holders of flash drives which can allow malicious programs to jump from PC to PC avoiding corporate firewalls, and small business subcontractors where much of your confidential information may reside.
2008 promises to be a bad year for computer users, especially those who use laptops and those in small businesses. Hackers are fast being replaced by organised criminal gangs and hostile state intelligence services, who are using the expertise of IT professionals to try to break into your systems to steal data. The weakest links are often inexperienced workstation users, or those who like to forward “funny” emails, laptop users, those who use home PCs for work purposes, holders of flash drives which can allow malicious programs to jump from PC to PC avoiding corporate firewalls, and small business subcontractors where much of your confidential information may reside.The UK Information Commissioner has warned that in cases of ID data theft, lack of awareness of the threats and inadequate countermeasures will not be a defence to either corporate or individual prosecution.
The US Government has set up an excellent Web site to warn computer users of the growing threats, and you can subscribe to a range of alerts:
http://onguardonline.gov/certalerts.html
Contact Nicky for more information on the forthcoming Information and IT Security Workshop, 7 April 2008.
Bomb Chemicals 'Can be Smuggled on Airplane'
Terrorists could smuggle the components needed to make a bomb on board a plane in Britain despite restrictions on carrying liquids in hand luggage, a television documentary has alleged. The show’s researchers mixed together several unidentified chemicals which were odourless, colourless and contained in bottles of less than 100ml (the enforced limit at most airports worldwide). They then placed the ‘bomb’ inside a decommissioned aircraft and detonated it using a commercial detonator. The resulting blast blew a hole in the side of the aircraft and snapped the ribs of the fuselage, damage that would be enough to make the pilot lose control of the aircraft were it to happen in mid-air.
Critics of the current approach to aviation security in the UK claim that screening of and restrictions on hand luggage remains ineffective without screening and profiling of passengers themselves.
Read on at:
http://www.telegraph.co.uk/news/main.jhtml?xml=/news/2008/02/26/nbomb126.xml
Critics of the current approach to aviation security in the UK claim that screening of and restrictions on hand luggage remains ineffective without screening and profiling of passengers themselves.
Read on at:
http://www.telegraph.co.uk/news/main.jhtml?xml=/news/2008/02/26/nbomb126.xml
Gunboat Escorts and Armed Security Patrols for LNG Tanker Ships, as Well as Aerial and Video Surveillance and Underwater Checks
 Security measures for a proposed LNG terminal near Baltimore, Chesapeake Bay, have been rejected by the US Coastguard, on the grounds that security measures for LNG tankers loaded with in excess of 200,000 cubic metres of LNG, navigating through a bay lined with residential settlements need to be on a wholly different scale to those applicable to a sea-facing terminal.
Security measures for a proposed LNG terminal near Baltimore, Chesapeake Bay, have been rejected by the US Coastguard, on the grounds that security measures for LNG tankers loaded with in excess of 200,000 cubic metres of LNG, navigating through a bay lined with residential settlements need to be on a wholly different scale to those applicable to a sea-facing terminal.Amongst the enhanced security measures is a plan to provide gunboat escorts, armed security patrols, towing vessels, aerial surveillance, video surveillance, underwater security sweeps and a way to deal with passing cruise ships.
For more on this story click here.
Training Tomorrow's Security Surveyors

The Elysium Paphos is one of Cyprus’ most prestigious hotels, favoured by several celebrities and royals. This week the hotel has been host to the Security Survey and Design Course, and, unusually, has been itself the subject of the survey study.
After one and a half days of formal input on security risk analysis, security design and survey methodology, the eight participants set about a comprehensive survey study of the 300-room property, requiring day and night inspections. Due to the special nature of this type of business, which has a very broad spectrum of threat sources and targets, course participants have been working especially hard on the risk analysis, visiting all back-of-house areas and interviewing key supervisors and front line staff.
After one and a half days of formal input on security risk analysis, security design and survey methodology, the eight participants set about a comprehensive survey study of the 300-room property, requiring day and night inspections. Due to the special nature of this type of business, which has a very broad spectrum of threat sources and targets, course participants have been working especially hard on the risk analysis, visiting all back-of-house areas and interviewing key supervisors and front line staff.
The next task for participants, working as syndicates, is to produce survey reports and to deliver a management presentation. With just two days left, and two evening feasts to attend this is going to be a tall order!
The course is led by David Cresswell MSc CPP PSP.
The next Security Surveying and Design Course takes place in the UK, 21-25 April. Contact Janet for details.
Wednesday, March 12, 2008
The Insider Threat
One of the biggest threats all business and security organisations have to face is the ‘insider’.
Despite all the physical and electronic security measures, policies and procedures, an employee who turns ‘bad’ for whatever reasons, is quite often extremely difficult to detect, unless they become careless or greedy. Two members of the economic crime division are guest speakers at the ASIS UK ‘Spring’ seminar in London on 19 March, and have agreed to provide a very detailed insight into the world of the ‘insider’s‘ ideology and their, in some cases, very clever methodologies. Due to the nature of the subject and the examples they will be discussing ‘Chatham House’ rules will be applied.
You are encouraged to come along and join us at what will prove to be a valuable insight into the threat that lies dormant in every business and organisation.
Mike Alexander
Vice Chairman
ASIS UK Chapter 208
Details here.
Despite all the physical and electronic security measures, policies and procedures, an employee who turns ‘bad’ for whatever reasons, is quite often extremely difficult to detect, unless they become careless or greedy. Two members of the economic crime division are guest speakers at the ASIS UK ‘Spring’ seminar in London on 19 March, and have agreed to provide a very detailed insight into the world of the ‘insider’s‘ ideology and their, in some cases, very clever methodologies. Due to the nature of the subject and the examples they will be discussing ‘Chatham House’ rules will be applied.
You are encouraged to come along and join us at what will prove to be a valuable insight into the threat that lies dormant in every business and organisation.
Mike Alexander
Vice Chairman
ASIS UK Chapter 208
Details here.
ASIS UK Regional Event – Manchester – 24th April 2008 – All Welcome!
Security by Design with a Twist – Relevance to Corporate Activity
John Dwyer, a former Assistant Chief Constable of Cheshire Police. John will be speaking around “Buildings and Processes”.
Construction Design and Management Regulations 2007 – Strategies for Effective Compliance
David Maddock will explain the responsibilities of duty holders and how to effectively assess risks as well as the implications for safety and security.
Handling IT Security Breaches in the Workplace
Anna Cutts is a consultant specialising in intelligent business analysis.
Welcome to the Future of Security Qualifications
Janet Ward will explain ASIS Asset Protection Training and the linkage to Continuous Professional Development.
For more details click here.
John Dwyer, a former Assistant Chief Constable of Cheshire Police. John will be speaking around “Buildings and Processes”.
Construction Design and Management Regulations 2007 – Strategies for Effective Compliance
David Maddock will explain the responsibilities of duty holders and how to effectively assess risks as well as the implications for safety and security.
Handling IT Security Breaches in the Workplace
Anna Cutts is a consultant specialising in intelligent business analysis.
Welcome to the Future of Security Qualifications
Janet Ward will explain ASIS Asset Protection Training and the linkage to Continuous Professional Development.
For more details click here.
Don’t Rule out Being Attacked by Female Suicide Bombers
 According to the Associated Press, the U.S. military recently announced the capture of an insurgent leader who was recruiting and training women, including his wife, to wrap themselves in explosives and blow themselves up — the latest sign that al-Qaeda in Iraq plans to keep using women to carry out suicide attacks.
According to the Associated Press, the U.S. military recently announced the capture of an insurgent leader who was recruiting and training women, including his wife, to wrap themselves in explosives and blow themselves up — the latest sign that al-Qaeda in Iraq plans to keep using women to carry out suicide attacks.In some environments women have made up almost 20% of suicide attacks, dispelling unhelpful myths that suicide bombers are motivated by some sort of carnal reward in heaven. On 5th July 2003 two women, dressed in western clothes, blew themselves up at the entrance to a pop concert in Moscow, killing 14. In August 2004, also in Russia, two women suicide bombers blew themselves up minutes apart in mid-air, destroying two airliners.
Managing the Threat from Activism

Last year saw an escalation in Greenpeace invasions of coal-fired power stations. This year has seen a Greenpeace invasion of Heathrow Airport. The latest report from Associated Press indicates that things are heating up on the eco-warrior front:
Three seven-figure dream homes went up in flames early Monday in a Seattle suburb, apparently set by eco-terrorists who left a sign mocking the builders' claims that the 4,000-plus-square-foot houses were environmentally friendly. The sign - a sheet marked with spray paint - bore the initials ELF, for Earth Liberation Front, a loose collection of radical environmentalists that has claimed responsibility for dozens of attacks since the 1990s.
The Earth Liberation Front is an international underground network that uses violent direct action to sabotage corporations and government agencies that it alleges profit from the systematic destruction of the natural environment. The organization is most active in the US, where it is regarded by the FBI, although not the courts, as a domestic terrorist threat.
http://www.earthliberationfront.com/elf_news.htm
Wikipedia carries a good explanation of the ELF, a description which has earned the approval of an ELF spokesperson!:
http://en.wikipedia.org/wiki/Earth_Liberation_Front
ARC Training recommends that organizations, particularly those in Europe, North America and Australasia, take the following actions in view of this increased threat:
1. Review their threat and risk assessments in an effort to identify business activities that could cause them to become a target of such organizations.
2. Review physical security with particular regard to defending against, detecting and responding to a facility invasion.
3. Remain vigilant to insider assistance. Many of these organizations have sympathisers who have penetrated large corporations.
4. Monitor the activist calendar. 1st April, for example, is a day of action.
Three seven-figure dream homes went up in flames early Monday in a Seattle suburb, apparently set by eco-terrorists who left a sign mocking the builders' claims that the 4,000-plus-square-foot houses were environmentally friendly. The sign - a sheet marked with spray paint - bore the initials ELF, for Earth Liberation Front, a loose collection of radical environmentalists that has claimed responsibility for dozens of attacks since the 1990s.
The Earth Liberation Front is an international underground network that uses violent direct action to sabotage corporations and government agencies that it alleges profit from the systematic destruction of the natural environment. The organization is most active in the US, where it is regarded by the FBI, although not the courts, as a domestic terrorist threat.
http://www.earthliberationfront.com/elf_news.htm
Wikipedia carries a good explanation of the ELF, a description which has earned the approval of an ELF spokesperson!:
http://en.wikipedia.org/wiki/Earth_Liberation_Front
ARC Training recommends that organizations, particularly those in Europe, North America and Australasia, take the following actions in view of this increased threat:
1. Review their threat and risk assessments in an effort to identify business activities that could cause them to become a target of such organizations.
2. Review physical security with particular regard to defending against, detecting and responding to a facility invasion.
3. Remain vigilant to insider assistance. Many of these organizations have sympathisers who have penetrated large corporations.
4. Monitor the activist calendar. 1st April, for example, is a day of action.
30 Terrorist Groups 'Actively Watched' In UK
According to the Metro newspaper, quoting the Chief Constable of West Yorkshire Police at a national counterterrorism conference, 30 priority terrorist groups are currently under active surveillance. A further 200 support groups are in existence and, in addition, up to 2,000 "people of interest" are getting infrequent monitoring and surveillance.
For more on this story click here.
For more on this story click here.
Tuesday, March 11, 2008
Planning a New Access Control System? – Some Design Tips
HID Director of Technology Michael L Davis, writing in India Safe - India’s leading security magazine - has some useful points for security managers to bear in mind when installing a new access control system:
· The most secure card reader is a contactless smart card reader with manual authentication, the least is a CSN or “universal” card reader, which should not be used.
· Install the security systems wires in conduits. This makes it more difficult for perpetrators to locate the correct conduit or access the wires, increasing the chance of detection.
· Securely and permanently connect wiring to outside readers by soldering and covering connections with shrink wrap tubing.
· Secure readers and security components with security screws which require special tools to remove. Failed attacks will result in damage around the screws, check for this periodically.
· Ensure card readers have a tamper-detect mechanism, ideally this will also detect tampering with connecting wires.
· In sensitive locations CCTV should monitor both the reader and the door.
· Some readers are able to send “health” or “I’m alive” signals periodically upstream. Set them to occur faster than it would take to install a rogue device, ideally at one second intervals.
· Converge physical and logical access control systems to enable “geographical” monitoring, whereby a card user cannot gain access to one location whilst registered present at another. This can also ensure users can only access computers at a site after registering at a specified perimeter reader.
· Use biometric information in conjunction with card readers at high security sites. For example hand-held biometric fobs which only release RFID card data after a biometric authentication process has taken place.
· Use a proprietary format for cards which cannot be easily obtained illegally, preferably one that is site specific.
The full article can be accessed by clicking here.
Access Control is one of the core security management subjects covered in the forthcoming university-accredited Security Management Stage 1 Course, 31 March – 11 April. The course may be used as one of six modules that constitute a work-based studies MSc in conjunction with Middlesex University. Contact Janet for details.
· The most secure card reader is a contactless smart card reader with manual authentication, the least is a CSN or “universal” card reader, which should not be used.
· Install the security systems wires in conduits. This makes it more difficult for perpetrators to locate the correct conduit or access the wires, increasing the chance of detection.
· Securely and permanently connect wiring to outside readers by soldering and covering connections with shrink wrap tubing.
· Secure readers and security components with security screws which require special tools to remove. Failed attacks will result in damage around the screws, check for this periodically.
· Ensure card readers have a tamper-detect mechanism, ideally this will also detect tampering with connecting wires.
· In sensitive locations CCTV should monitor both the reader and the door.
· Some readers are able to send “health” or “I’m alive” signals periodically upstream. Set them to occur faster than it would take to install a rogue device, ideally at one second intervals.
· Converge physical and logical access control systems to enable “geographical” monitoring, whereby a card user cannot gain access to one location whilst registered present at another. This can also ensure users can only access computers at a site after registering at a specified perimeter reader.
· Use biometric information in conjunction with card readers at high security sites. For example hand-held biometric fobs which only release RFID card data after a biometric authentication process has taken place.
· Use a proprietary format for cards which cannot be easily obtained illegally, preferably one that is site specific.
The full article can be accessed by clicking here.
Access Control is one of the core security management subjects covered in the forthcoming university-accredited Security Management Stage 1 Course, 31 March – 11 April. The course may be used as one of six modules that constitute a work-based studies MSc in conjunction with Middlesex University. Contact Janet for details.
Selecting a Portable Explosives Detector? Many Are Not Fit for Purpose!
 Unfortunately, not all bombs look as obvious as the one pictured.
Unfortunately, not all bombs look as obvious as the one pictured.If you are considering purchasing a portable explosives detector you should ensure that you select only those devices which:
1. Have the ability for particulate detection. (Vapour detection alone is ineffective).
1. Have the ability for particulate detection. (Vapour detection alone is ineffective).
2. Are able to detect acetone-based home made explosives such as TATP.
With this in mind your choice should quickly narrow down to two models: The EVD 3500 (target price $31,000) and the Sabre 4000 (target price $26,000).
Older models such as the EVD 3000 are not able to detect TATP, the weapon of choice of self-starter Al-Qaeda cells.
If you are using anything less than these and you are reconnoitred by Al-Qaeda, they will know immediately that they are smarter than you and that you therefore represent a viable target!
Cyber Security Becomes a Corporate Governance Issue
 Delegates attending the recent Security Management Stage 2 Course in Kuala Lumpur to part in a discussion led by tutor David Cresswell about the increasing exposure of corporate IT systems - especially SCADA systems controlling critical processes - to cyber attack from sophisticated criminal and terrorist networks.
Delegates attending the recent Security Management Stage 2 Course in Kuala Lumpur to part in a discussion led by tutor David Cresswell about the increasing exposure of corporate IT systems - especially SCADA systems controlling critical processes - to cyber attack from sophisticated criminal and terrorist networks.The continued and growing reliance on networked operations, wireless systems and the globalization of information technology make private sector susceptibility to a cyber attack a material concern for the corporate sector, especially those elements which make up a nation’s critical national infrastructure (CNI). This is a concern so important that it now squarely falls within the duty of care that directors and officers owe their shareholders. They can no longer simply hide behind the "techies."
In the US, Department of Homeland Security Secretary Michael Chertoff has stated that cyber-security would be one of his department's principal focuses in 2008. Along with Homeland Security, the Director of National Intelligence and the US Overseas Security Advisory Council have labelled cyber-security one of the most pressing security concerns for 2008. For more information click here.
The next Security Management Stage 2 Course takes place in the UK, 30 June – 11 July.
A new ARC Training Course, Protecting Critical Infrastructure, will take a more detailed look at CNI vulnerability to cyber attacks from organised adversaries. The course takes place in the UK from 14-18 July.
For more information click here.
Terrorism Expert Bruce Hoffman Sets out 10 Things the US Ought to Know about Terrorism
 Message 4 of 10:
Message 4 of 10:Countering terrorism should not rely only on military operations. "Soft power" is equally essential. Hoffman defined that as information, economic development, political reform, and local empowerment. Military force can temporarily weaken or eliminate terrorists' capacity to attack. But that only addresses the immediate threat. A successful counter-terrorist policy combines military force with "soft power" over the long term. The goal should be not just to kill and capture terrorists but to break the cycle of recruitment and regeneration that sustains terrorist movements.
Read the full text here.
Protection against Explosive Devices and the Corporate Response to Terrorism are two topics covered in open programmes by ARC Training. For more information, contact Janet.
Holland Raises Domestic Terror Alert
The Netherlands last week raised its terrorism alert level to "substantial", partly due to the expected release of an anti-Islam film, reports the BBC.
It is the second-highest alert level, although the justice ministry said "there is no concrete evidence" that the country faced possible attacks.
The move comes as far-right Dutch MP Geert Wilders prepares to air his film, which has already angered Muslims. Mr Wilders has said the film is about the Koran, but gave few details.
Meanwhile, many in the Arab world have joined a boycott against Danish food products following a reigniting by Denmark of the cartoon controversy.
It is the second-highest alert level, although the justice ministry said "there is no concrete evidence" that the country faced possible attacks.
The move comes as far-right Dutch MP Geert Wilders prepares to air his film, which has already angered Muslims. Mr Wilders has said the film is about the Koran, but gave few details.
Meanwhile, many in the Arab world have joined a boycott against Danish food products following a reigniting by Denmark of the cartoon controversy.
Germany Curbs Government Spying on Computers
Germany's highest court has restricted the right of the security services to spy on the computers of suspected criminals and terrorists.
Under the technique, software sent in an email enables the authorities to spy on a suspect's computer hard drive. The Federal Constitutional Court in Karlsruhe said cyber spying violated individuals' right to privacy and could be used only in exceptional cases. (Similar software is used by criminal spies, who lure unsuspecting email recipients to open attachments).
Civil liberties activists have warned of an unacceptable invasion of privacy.
Meanwhile, Britain continues to be close to the top of the surveillance society league, according to a recent report in The Economist, and most of us are not particularly bothered, if it ensures our security, polls consistently confirm.
Under the technique, software sent in an email enables the authorities to spy on a suspect's computer hard drive. The Federal Constitutional Court in Karlsruhe said cyber spying violated individuals' right to privacy and could be used only in exceptional cases. (Similar software is used by criminal spies, who lure unsuspecting email recipients to open attachments).
Civil liberties activists have warned of an unacceptable invasion of privacy.
Meanwhile, Britain continues to be close to the top of the surveillance society league, according to a recent report in The Economist, and most of us are not particularly bothered, if it ensures our security, polls consistently confirm.
When Can Telephone Intercepts Become Evidence?
 With legal systems largely based on the English common law model, the US, Canada, New Zealand, Ireland, Australia, Hong Kong and South Africa all allow certain kinds of intercept evidence in their courts of law.
With legal systems largely based on the English common law model, the US, Canada, New Zealand, Ireland, Australia, Hong Kong and South Africa all allow certain kinds of intercept evidence in their courts of law.But Britain's security services fear that allowing intercept evidence to be used in a court of law would undermine its work.
Read the pros and cons of telephone intercept evidence here.
Thursday, March 6, 2008
Security Management Training - Forthcoming Events

31 March – 11 April
Security Management Stage 1
(postgraduate university accredited)
3 April
Protection against Explosive Devices Workshop
7 April
Information and IT Security Workshop
8 April
Crisis Management Workshop
21-25 April
Security Surveying and Design
12-23 May
Security Management Stage 3
(postgraduate university accredited)
14 May
Kidnap Risk Reduction and Response Workshop
19 May
Business Espionage and Investigating Information Leaks
2-4 June
Retail and Supply Chain Security Management
23-27 June
Advanced Investigation Techniques
30 June – 11 July
Security Management Stage 2
(postgraduate university accredited)
30 June
Warning - April 1st
Rising Tide and associated activist organisations are planning a day of action on April 1st, coined Fossil Fools Day. This may coincide with a Greenpeace invasion of a coal-fired power station or an action targeting an oil facility.
A quote from their website:
http://www.fossilfoolsday.org/
"Target a local fossil fool - See the clowns investing in coal - The carbon offset contortionist or the oily strong man? and join with thousands around the world in taking one step closer to dismantling the fossil fuel industry. Find a fossil fool in your community and pull a prank that packs a punch."
A quote from their website:
http://www.fossilfoolsday.org/
"Target a local fossil fool - See the clowns investing in coal - The carbon offset contortionist or the oily strong man? and join with thousands around the world in taking one step closer to dismantling the fossil fuel industry. Find a fossil fool in your community and pull a prank that packs a punch."
Battery Operated UAVs Scan for Suspicious Behaviour in Crowds - The Surveillance Society
 These days, reports The Economist, data about people's whereabouts, purchases, behaviour and personal lives are gathered, stored and shared on a scale that no dictator of the old school ever thought possible. Most of the time, there is nothing obviously malign about this. Governments say they need to gather data to ward off terrorism or protect public health; corporations say they do it to deliver goods and services more efficiently. But the ubiquity of electronic data-gathering and processing—and above all, its acceptance by the public—is still astonishing, even compared with a decade ago.
These days, reports The Economist, data about people's whereabouts, purchases, behaviour and personal lives are gathered, stored and shared on a scale that no dictator of the old school ever thought possible. Most of the time, there is nothing obviously malign about this. Governments say they need to gather data to ward off terrorism or protect public health; corporations say they do it to deliver goods and services more efficiently. But the ubiquity of electronic data-gathering and processing—and above all, its acceptance by the public—is still astonishing, even compared with a decade ago.In Britain, Italy and America, police are experimenting with the use of miniature remote-controlled drone aircraft, fitted with video cameras and infra-red night vision, to detect “suspicious” behaviour in crowds. Weighing no more than a bag of sugar and so quiet that it cannot be heard (or seen) when more than 50 metres (150 feet) from the ground, the battery-operated UAV (unmanned aerial vehicle) can be flown even when out of sight by virtue of the images beamed back to a field operator equipped with special goggles. MW Power, the firm that distributes the technology in Britain, has plans to add a “smart water” spray that would be squirted at suspects, infusing their skin and clothes with genetic tags, enabling police to identify them later.
ID Theft - Unprotected PCs Connected to Internet Are Compromised within Minutes
 Research by Symantec shows that an unprotected computer connected to the Internet will be attacked remotely within minutes. Apart from the obvious danger of the user’s ID theft, unprotected home PCs can remotely be hooked into networks of zombie computers being used to spread spam, steal other peoples’ IDs and attack websites.
Research by Symantec shows that an unprotected computer connected to the Internet will be attacked remotely within minutes. Apart from the obvious danger of the user’s ID theft, unprotected home PCs can remotely be hooked into networks of zombie computers being used to spread spam, steal other peoples’ IDs and attack websites.Despite this, many organisations fail to issue guidelines to workers who use their home PCs for work-related issues, such as emails. At very least, a full check of the PC should be carried out by a competent person, and a comprehensive anti-virus/anti-spyware/firewall program, such as Norton 360, should be installed. Anti-spyware programs, in particular, should have the ability to both firewall and sweep automatically, and should be obtained from reputable sources – some anti-spyware software is spyware in disguise.
Meanwhile, blog readers may recall that in June 2007 the FBI announced that it was trying to contact more than 1 million home PC owners who have unknowingly had their computers remotely hijacked by cyber-criminals. Once hijacked, PCs can be used to send out spam, spread spyware or as repositories for illegal content such as pirated movies or pornography, and most owners will not be aware that their machines have been taken over. For more read here.
Spyware and other related threats are discussed in the one-day IT and Information Security session on Security Management Stage 1, 31 March – 11 April 2008. The workshop may also be attended as a stand-alone module on 7 April. For more information on this, and to discuss in-house information security awareness training for staff, contact Janet.
And Who Are You? – Privacy International Launches Campaign to Protect Individuals against ID Fraud
I received a call from a national bank yesterday presumably trying to sell me something. Before the bank would tell me what it was they were trying to sell me, they asked me to confirm some personal details about myself. I challenged this as I have no way of knowing if the person I am talking to is an employee of the bank or a fraudster. The employee offered to give me her employee number, but this is of no value to me as I have nothing to reference it against.
Purely by coincidence, a little later I came across a campaign on the Web site of Privacy International calling on banks to act more responsibly in the face of an identity theft onslaught. It is difficult to keep up with the myriad of methods now employed by fraudsters to steal people’s ID information. Therefore, Privacy International believes that companies and government have a responsibility to verify their own identity before requiring customers to divulge such information, and sets out a security methodology for achieving this. See:
http://www.privacyinternational.org/article.shtml?cmd%5b347%5d=x-347-559750
I am not a fan of pressure groups or NGOs, but I think in the case of ID theft UK banks have a moral duty to protect us from ID thieves. The disruption of even debit card fraud is significant - I should know as I have been a victim.
It should be the banks, rather than PI, which should lead the fight against fraudsters. For example, despite receiving daily phishing emails from almost every high street bank in the UK, and despite having accounts with three of them, I have never once received a letter from the banks warning me not to respond to emails purporting to come from them.
An example of a responsible banking security practice was highlighted recently by an Indian delegate, whose bank, ICICI - the largest private sector bank in India - sends him an SMS message every time there is a transaction on his account.
Oh to have had the benefit of this facility from my bank when my own account was raided three times in as many days in 2006 by ID fraudsters!
Purely by coincidence, a little later I came across a campaign on the Web site of Privacy International calling on banks to act more responsibly in the face of an identity theft onslaught. It is difficult to keep up with the myriad of methods now employed by fraudsters to steal people’s ID information. Therefore, Privacy International believes that companies and government have a responsibility to verify their own identity before requiring customers to divulge such information, and sets out a security methodology for achieving this. See:
http://www.privacyinternational.org/article.shtml?cmd%5b347%5d=x-347-559750
I am not a fan of pressure groups or NGOs, but I think in the case of ID theft UK banks have a moral duty to protect us from ID thieves. The disruption of even debit card fraud is significant - I should know as I have been a victim.
It should be the banks, rather than PI, which should lead the fight against fraudsters. For example, despite receiving daily phishing emails from almost every high street bank in the UK, and despite having accounts with three of them, I have never once received a letter from the banks warning me not to respond to emails purporting to come from them.
An example of a responsible banking security practice was highlighted recently by an Indian delegate, whose bank, ICICI - the largest private sector bank in India - sends him an SMS message every time there is a transaction on his account.
Oh to have had the benefit of this facility from my bank when my own account was raided three times in as many days in 2006 by ID fraudsters!
Insiders and Google Earth Show Demonstrators the Way in
 Source: Sunday Times
Source: Sunday TimesDemonstrators revealed yesterday that they had used Google Earth to plot their protest on the roof of the Houses of Parliament last week against the expansion of Heathrow.
The website, which allows users to zoom in on satellite photographs of Earth, “showed us all the walkways, steps and other details we needed to make our way across the roof from the door to the far side where the public could see us”, said Leo Murray, one of the five protesters. The planning for the stunt began last autumn after the government published documents for a public consultation on a possible third runway at Heathrow.
Tamsin Omond, a 23-year-old with a first-class degree in English literature from Cambridge, described how they were able to map out the interior of the Palace of Westminster without raising suspicions. “We sent in a reconnaissance group who simply wandered around till they found the route to the roof ending in an open door. The fag butts around it showed it was being used by smokers,” she said.
They managed to recruit a young Commons insider who, thanks to having a security pass, was able to carry the banners, handcuffs (bought from a Soho sex shop) and other equipment past the body scanners and X-ray machines that are supposed to protect the buildings.
Don't forget that April 1st is Fossil Fools Day - be vigilant against attack if you are in the energy sector!
Wednesday, March 5, 2008
Security Management - Do Individuals with Regular Business Backgrounds Make Better Security Leaders?
 Individuals with government backgrounds held a monopoly on security positions throughout the 1970s as businesses sought out their knowledge of physical security, criminal justice and investigation, reports the website Securitysolutions.com.
Individuals with government backgrounds held a monopoly on security positions throughout the 1970s as businesses sought out their knowledge of physical security, criminal justice and investigation, reports the website Securitysolutions.com.But in the 1980s, it all began to change. For 20 years, many organizations had experienced a growing culture clash with their government-trained security leaders, who often adopted a “my way or the highway” attitude in managing their departments and in communicating with other business units and executives.
Corporations began looking for security leaders who knew and understood their company's culture and could work within it — rather than forcing it into submission. They sought out new blood with an understanding of their internal processes, a familiarity with their employees, institutional memory and knowledge of the brand, customers and business. Where better to look than in the organization itself? Management saw the value of promoting security executives either from within the security department or from elsewhere within the business.
Intrigued or infuriated? Read the pros and cons of this apparent trend here.
Security leadership is examined in great detail on the Security Management Stage 2 Course, 30 June – 11 July. The course is led by Peter Horsburgh CPP PSP, who has twice been a corporate head of security.
Corporations began looking for security leaders who knew and understood their company's culture and could work within it — rather than forcing it into submission. They sought out new blood with an understanding of their internal processes, a familiarity with their employees, institutional memory and knowledge of the brand, customers and business. Where better to look than in the organization itself? Management saw the value of promoting security executives either from within the security department or from elsewhere within the business.
Intrigued or infuriated? Read the pros and cons of this apparent trend here.
Security leadership is examined in great detail on the Security Management Stage 2 Course, 30 June – 11 July. The course is led by Peter Horsburgh CPP PSP, who has twice been a corporate head of security.
Security Management Training - Not Only Was Last Week a Learning Experience, It Was Also One of The Most Enjoyable Courses I've Been on!
 "Not only was last week a learning experience, it was also one of the most enjoyable courses I've been on!"
"Not only was last week a learning experience, it was also one of the most enjoyable courses I've been on!"Comments received about the Security Coordination and Management Course from a UK security manager of the global market leader in providing photographic products and services.
The sentiments were echoed by a country head of security for the world's leading mobile phone supplier, who described the course as a “wonderful experience”.
The next Security Coordination and Management Course takes place in the UK 1-5 September. If you can’t wait until then, David Cresswell will be conducting the programme in Oman, in the Arabian Gulf, 20-24 April.
The Threat of Terror is Never Far Away – Arrests in Saudi Avert Another Campaign
Saudi authorities have arrested 28 people thought to be rebuilding the al-Qaeda terror network in Saudi Arabia, a Saudi government spokesman has said. In December, Saudi authorities arrested a further 28 people believed to be plotting attacks on Mecca and Medina during the Hajj pilgrimage.
Businesses in the Arabian Gulf should be on constant alert to the threat of terrorism, and your attention is drawn to the recent guidelines issued by London’s Met Police on indications of possible targeting:
http://www.met.police.uk/so/at_hotline.htm
(But if you are not in the UK please don’t call the Met’s hotline!!)
For UK readers, the City of London Police will be giving an update on the fight against terrorism in London at the forthcoming ASIS Spring Seminar, 19th March. Click below for more information.
http://www.asis.org.uk/eventscalendar.html
Businesses in the Arabian Gulf should be on constant alert to the threat of terrorism, and your attention is drawn to the recent guidelines issued by London’s Met Police on indications of possible targeting:
http://www.met.police.uk/so/at_hotline.htm
(But if you are not in the UK please don’t call the Met’s hotline!!)
For UK readers, the City of London Police will be giving an update on the fight against terrorism in London at the forthcoming ASIS Spring Seminar, 19th March. Click below for more information.
http://www.asis.org.uk/eventscalendar.html
Security Surveying on the Island of Love
 David Cresswell heads off to Cyprus next week to conduct training for nine delegates from six different countries, who will be descending on the seaside resort of Pafos to take part in one of ARC’s most popular programmes, the week long Security Survey and Design (SSD) Course.
David Cresswell heads off to Cyprus next week to conduct training for nine delegates from six different countries, who will be descending on the seaside resort of Pafos to take part in one of ARC’s most popular programmes, the week long Security Survey and Design (SSD) Course.The SSD Course is very practical, and delegates get the opportunity, under tutor supervision, to carry out a detailed security survey of a working business. Then, in syndicates, they are required to produce survey reports and to present their results at a management presentation, during which their security recommendations come under scrutiny from those who control the purse strings!
Almost one hundred security manager delegates have now attended security surveying training with ARC, going on to save their organisations many tens of thousands of dollars on what would otherwise have been expensive consultant-surveyor costs.
Some companies chose to run the course in-house, thereby training an entire team of security managers at one time in order to establish an internal peer-surveying capability.
The next SSD course takes place in the UK, 21-25 April. Contact Janet for more details.
Baroness Henig, Chair of the Security Industry Authority to Present Certificates to Successful CPP and PSP Candidates
 A record 34 security professionals passed the ASIS CPP and PSP certification examinations, held in the UK on 3rd November 2007.
A record 34 security professionals passed the ASIS CPP and PSP certification examinations, held in the UK on 3rd November 2007.On 18th March Baroness Henig, Chair of the Security Industry Authority (SIA), will be presenting certificates to the successful candidates at a special dinner arranged in their honour.
Proposals for regulation of the security consultancy sector will be published for consultation in 2010 in a Regulatory Impact Statement. If this does eventually lead to the regulation of security consultancy, evidence of professional competence and relevant experience, such as that conferred by the CPP and PSP certifications, is sure to be an essential element in licensing.
Read all about Baroness Henig’s varied career and interests at:
http://en.wikipedia.org/wiki/Ruth_Henig,_Baroness_Henig
Tuesday, March 4, 2008
Indimedia Predicts Direct Action in Reaction to Arrest of Nigerian
Radical news organisation Indimedia is predicting an upsurge in direct action and violence following the detention of Nigerian Henry Okah. Oil companies are expected to bear the brunt of the protest.
Immediate Actions in the Event of a Bomb Explosion
 It seems likely that there will be a resurgence of Al-Qaeda terrorist attacks on mainland Europe this year, as the sheer volume of plots begins to overwhelm the capacity of intelligence and police resources to manage the threat.
It seems likely that there will be a resurgence of Al-Qaeda terrorist attacks on mainland Europe this year, as the sheer volume of plots begins to overwhelm the capacity of intelligence and police resources to manage the threat.Delegates attending ARC Training’s Security Management Stages 1 and 2 courses are being advised to plan for this and to have appropriate contingency responses in place. While it is more likely that public targets, such as airports, the transport infrastructure (stations, airports, buses, trains), sporting events and places of entertainment will bear the brunt of the attacks, bombing incidents in major business districts cannot be ruled out.
The much-hyped-up 2007 Glasgow Airport and London gas-bomb attacks were amateur, and wholly not indicative of the capabilities of many Al-Qaeda-inspired terrorists, who possess at least the theoretical know-how to detonate a devastating large vehicle improvised explosive device in the heart of a major city, causing destruction on a scale not seen since the height of the IRA campaign, and loss of life on a scale at least matching the 7/7 London mass public transport bombings.
One contingency planning step that organisations can take is to consider their immediate responses in the event of a nearby bomb detonation. Al-Qaeda has demonstrated an attraction to near simultaneous bomb attacks, and the Atocha train bombings in Spain graphically illustrate how survivors fleeing from the first blasts were fatally caught up in subsequent blasts. Furthermore, experience from Tanzania tells us that a number of people were injured when they assembled at windows to look out on gunfire in the street, which preceded a bomb attack.
Immediately upon being aware that an external blast has occurred, staff should assume that a second blast may follow and should take cover immediately, avoiding all external and internal glazing. A decision should then be taken as to where staff are safest. This requires pre-planning, a good internal communications systems, and a responsible person on duty at all times who can take charge.
For further information on protecting your staff against explosive devices, contact David.
Research Published on the Web Site CSOonline Reveals Huge Breaches in Staff Information Security Practices
 Both the Security Management Stages 1 and 2 courses address the issue of information and IT security in detail. As part of a workshop, delegates are asked to benchmark their organisation’s adherence to IT and information security best practice on a scale of 1-10. Unsurprisingly, most, especially those who represent multinational companies, self score at between 8-9.
Both the Security Management Stages 1 and 2 courses address the issue of information and IT security in detail. As part of a workshop, delegates are asked to benchmark their organisation’s adherence to IT and information security best practice on a scale of 1-10. Unsurprisingly, most, especially those who represent multinational companies, self score at between 8-9.But if the results of recent research published on CSO online are anything to go by, policies and compliance may be at opposite ends of the spectrum in many organisations. The survey findings are as follows:
1. Copying confidential information onto a USB memory stick: Eighty-seven percent of respondents believe their company’s policy forbids it, yet 51 percent say they do it anyway.
2. Accessing web-based e-mail accounts from a workplace computer: Forty-five percent of those surveyed use webmail at work; 74 percent say there is no stated policy that forbids it.
3. Losing a portable data-bearing device: Thirty-nine percent of respondents say they have lost or misplaced such a device, and 72 percent of them did not report the lost device immediately.
4. Downloading personal software onto a company computer: Sixty percent of respondents say there is no stated policy that forbids downloading personal software, a practice that 45 percent of respondents admit to.
5. Sending workplace documents as an attachment in e-mail: Thirty-three percent of respondents send work documents as attachments, and 48 percent aren’t even sure whether or not that violates policy.
6. Disabling security and firewall settings: Eighty percent of those surveyed don’t know whether disabling security is against policy; 17 percent of respondents do it.
7. Sharing passwords with co-workers: Sixty-seven percent say the company’s policy forbids sharing passwords, but 46 percent of them do it anyway.
The next Security Management Stage 1 Course takes place 31 March – 11 April.
The next Security Management Stage 1 Course takes place 31 March – 11 April.
Part of the course is a one day workshop on 7 April, Information and IT Security Management, which is also open to day delegates. This workshop can also be conducted in house to increase staff awareness of IT and information security issues. Contact Janet for details.
Met Police Launch New Anti-Terrorism Campaign and Call for Public Help in Identifying the Following Suspicious Activities
 Source: http://cms.met.police.uk/news/publicity_campaigns/terrorism/met_launches_new_counter_terrorism_campaign_25_02_08
Source: http://cms.met.police.uk/news/publicity_campaigns/terrorism/met_launches_new_counter_terrorism_campaign_25_02_08The Met Police is asking all members of the public - people who live in London, as well as those who work in and visit the city - to trust their instincts and contact the Anti-Terrorist Hotline on 0800 789 321 with any information they have. No piece of information is considered too small.
"We want people to look out for the unusual - some activity or behaviour which strikes them as not quite right and out of place in their normal day to day lives." Terrorists live within our communities, making their plans whilst doing everything they can to blend in, and trying not to raise suspicions about their activities.
"They have a lot of work to do before they attack. They need money and may commit cheque, credit card and identity fraud to finance their activities.
"Terrorists use chemicals. Do you know someone buying large or unusual quantities of chemicals for no obvious reason? Handling chemicals is dangerous, and maybe you've seen goggles or masks dumped somewhere?
"Observation and surveillance help terrorists plan attacks. Have you seen anyone taking pictures of security arrangements such as CCTV? Has it made you suspicious?
"Meetings, training and planning for terrorist attacks can take place anywhere. Do you know someone who travels but is vague about where they're going?
"Terrorists use computers - do you know someone who visits terrorist-related websites?
The Insider Threat, Terrorism Funding and the Taser – What’s the Connection?
 The insider threat, terrorism funding, modern policing tactics against terrorism and public order, and the use of the Taser – these will be the topics under discussion at the forthcoming ASIS UK Spring Seminar in London on 19th March.
The insider threat, terrorism funding, modern policing tactics against terrorism and public order, and the use of the Taser – these will be the topics under discussion at the forthcoming ASIS UK Spring Seminar in London on 19th March.Taking the podium will be Chief Superintendent Alex Robertson, Detective Chief Inspector Richard Jack and Detective Constable Michael Rees.
Non-ASIS member are most welcome and registration should be made directly to Jude Awdry.
The event, which is held under Chatham House Rules, provides a unique opportunity to be briefed by front-line police officers and commanders on some very topical issues in terrorism and public order. And there is always time built in for difficult questions from the audience!
The insider threat is an issue which is currently vexing elements of the UK’s Critical National Infrastructure, and the CPNI have posted special guidelines on their web site.
Creeping deployment of the Taser stun gun is attracting controversy, especially in light of recent university research from the US which suggests this device is not as safe as its manufacturers have been claiming.
Welcome to a New Member of Staff (and another Cresswell!)

The blog would like to extend a warm welcome to Faith, who has joined the ARC team on a temporary 6-month assignment. Faith is David’s daughter and will be providing direct support to this much overworked MD!!
One of Faith’s first tasks has been to compile a searchable index of all (to date 470) blog articles. If you would like a copy of this ‘xls spreadsheet, please contact Faith direct by email.
Another task that she will take on is to provide additional support to those of you who are writing your post-course essays. If you need a particular topic researched, or if you would like your essay draft proofed, you may contact her and she will be pleased to assist.
She is also working on an ARC PSP Certification Study Guide, which it is hoped to complete in the next few weeks.
Finally, she is responsible for the new ARC web site, which we hope to have up and running in April.
Another task that she will take on is to provide additional support to those of you who are writing your post-course essays. If you need a particular topic researched, or if you would like your essay draft proofed, you may contact her and she will be pleased to assist.
She is also working on an ARC PSP Certification Study Guide, which it is hoped to complete in the next few weeks.
Finally, she is responsible for the new ARC web site, which we hope to have up and running in April.
The Most Popular Security Management Course in the World?
The university-accredited Security Management Stage 1 Course is arguably the most popular security management course in the world, having been attended by hundreds of delegates from literally around the globe, representing many of the world’s most successful companies.
The syllabus, which has been fully updated for 2008, includes:
Security Risk Management
Security Operations Management
Security Policies & Procedures
Security Design
Introduction to Investigations
Introduction to Security Surveying
Perimeter & Buildings Security
Access Management
Workplace Crime Prevention
Protection against Explosive Devices
Manpower Selection & Deployment
Leadership & Motivation
Information Security & TSCM
IT Security
Protection of At-Risk Personnel
Crisis Management
Change Management
Course Project
The next course takes place 31 March – 11 April in the Thames Valley. Contact Janet for more information.
The syllabus, which has been fully updated for 2008, includes:
Security Risk Management
Security Operations Management
Security Policies & Procedures
Security Design
Introduction to Investigations
Introduction to Security Surveying
Perimeter & Buildings Security
Access Management
Workplace Crime Prevention
Protection against Explosive Devices
Manpower Selection & Deployment
Leadership & Motivation
Information Security & TSCM
IT Security
Protection of At-Risk Personnel
Crisis Management
Change Management
Course Project
The next course takes place 31 March – 11 April in the Thames Valley. Contact Janet for more information.
Monday, March 3, 2008
The Spy in Your Server
 Who is spying on whom, and how? This 10th August 2000 article, written by veteran investigative journalist Duncan Campbell, is probably uncomfortably close to the truth, if the accuracy of Campbell’s previous 25 years of state eavesdropping exposes are anything to go by. Read on at:
Who is spying on whom, and how? This 10th August 2000 article, written by veteran investigative journalist Duncan Campbell, is probably uncomfortably close to the truth, if the accuracy of Campbell’s previous 25 years of state eavesdropping exposes are anything to go by. Read on at:How to protect your company's data from prying eyes (of competitors or foreign states) is one of many subjects covered in detail on Security Management Stage 1, 31 March - 11 April 2008. Contact Janet for more information.
Download the 10th Annual Ernst and Young Global Information Security Survey
 The 10th annual Ernst and Young Global Information Security Survey makes interesting reading.
The 10th annual Ernst and Young Global Information Security Survey makes interesting reading.The report draws particular attention to the growing integration of information security into enterprise risk management, an area in which physical and operational security practitioners should already be very active.
Unlike physical security, however, the key driver for infosec integration is regulatory compliance, as the following extract from the report explains:
A powerful message from this year’s survey is the proportion of respondents who acknowledge they have partially or fully integrated their information security functions with risk management operations (82%, compared with 40% in 2005 and 43% in 2006) with regulatory compliance as a major integration stimulus, the proportion of organisations that have fully integrated both functions nearly doubled, from 15% in 2006 to 29% in 2007.
Is this an indicator that information security will no longer be a part of the IT function? Ernst and Young don’t think so. Rather, this result substantiates a growing trend to integrate the information security function along strategic/governance lines for regulatory compliance and architectural lines within the IT function.
The Downside to Dynamic Return on Security Investment
 The Security Management Stage 2 session on Integrating and Specifying Security Technology addresses many key issues to do with new security technology, including how to create dynamic return on security investment – the ability of a new security system to provide enterprise-wide value-added benefits.
The Security Management Stage 2 session on Integrating and Specifying Security Technology addresses many key issues to do with new security technology, including how to create dynamic return on security investment – the ability of a new security system to provide enterprise-wide value-added benefits.An example of dynamic return on security investment is where a new enterprise-wide IP CCTV project is integrated with voice-over-Internet protocol (VoIP) telephony. In some cases, organisations with particularly heavy telephony usage are able to recover the costs of the CCTV installation in just one year from savings in traditional landline call charges.
But there is a downside to VoIP, as identified recently in Communications News, which predicts no less than five VoIP-associated threats:
But there is a downside to VoIP, as identified recently in Communications News, which predicts no less than five VoIP-associated threats:
1. Denial-of-service (DoS) and distributed DoS attacks on VoIP networks will become an increasingly important issue.
2. HTTP or other third-party data services running on VoIP end-points will be exploited for eavesdropping and other attacks.
3. The hacking community, experienced with exploiting the vulnerabilities in other Microsoft offerings, will turn its attention and tools toward Microsoft OCS.
4. Hackers will set up more IP PBXs for vishing/phishing exploits. Vishing bank accounts will accelerate, due to ease of exploit and the appeal of easy money.
5. VoIP attacks against service providers will escalate, using readily available, anonymous $20 SIM cards. Service providers are, for the first time, allowing subscribers to have direct access to mobile core networks over IP, making the spoofing of identities and use of illegal accounts to launch attacks easier.
Airport Demonstrations Show Security Gaps
 The UK media this week reported two separate demonstrations by environmental activists against the extension of airports and the construction of additional runways. The demonstrators managed to ensure the highest possible profile for their activities by breaching security at Heathrow Airport (climbing onto a BA aircraft tail) and the Houses of Parliament. In addition to the considerable embarrassment for security forces at both sites, questions will no doubt be raised about the methods and routes of access for the demonstrators:
The UK media this week reported two separate demonstrations by environmental activists against the extension of airports and the construction of additional runways. The demonstrators managed to ensure the highest possible profile for their activities by breaching security at Heathrow Airport (climbing onto a BA aircraft tail) and the Houses of Parliament. In addition to the considerable embarrassment for security forces at both sites, questions will no doubt be raised about the methods and routes of access for the demonstrators:- Had they carried out surveillance?
- Were they aided by insiders?
- What could have happened if they had been terrorists?
Incidents such as this throw up serious concerns for the security professional. And such groups appear to be stepping up their activities. Could it be your CEO’s 4x4 next? Or even his residence?
We discuss responses to threats such as these in detail during our courses. For more information contact Janet.
Subscribe to:
Posts (Atom)